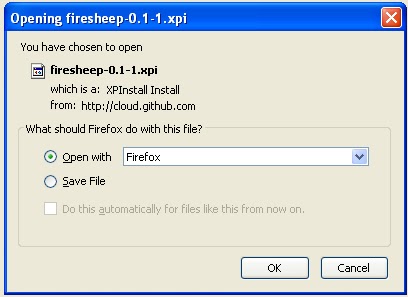
How to hack?, I get this question asked daily, Lots of people are curious to learn Ethical hacking but they do not know where to start, Any one can become a fairly good Ethical Hacker if he/she can learn from basics and he/she should have a place to practice what he learned
This is where The Hacker's Academy comes into play, If you are a beginner or intermediate or advanced this is still for you, The Hackers Academy is one of the most professional online Ethical Hacking and penetration testing institute, one of the best parts of hackers academy i like is that they give you labs(A place where you can practice) so you can try the concepts for your self
The course will contain of audio recording and video recordings but the most important part is that once you are a member of hackers academy they will tell you exactly how you can create Labs so you can practice what you have learned.
If you get stuck some where then they have professionals 24/7 there to help you out with any problem you have or any question you have. The Hackers Academy course will also prepare you for different types of certifications, once you become a member of The Hackers Academy and I can say it surely that you will pass any type of Ethical hacking certifications and tests
The membership program also has a 30 day money back guarantee, so you have nothing to loose!, If you are unhappy with them, then they will return your every penny
So what are you waiting for, Don't wait until you loose your chance!Get it now!
Continue Reading...
This is where The Hacker's Academy comes into play, If you are a beginner or intermediate or advanced this is still for you, The Hackers Academy is one of the most professional online Ethical Hacking and penetration testing institute, one of the best parts of hackers academy i like is that they give you labs(A place where you can practice) so you can try the concepts for your self
The course will contain of audio recording and video recordings but the most important part is that once you are a member of hackers academy they will tell you exactly how you can create Labs so you can practice what you have learned.
If you get stuck some where then they have professionals 24/7 there to help you out with any problem you have or any question you have. The Hackers Academy course will also prepare you for different types of certifications, once you become a member of The Hackers Academy and I can say it surely that you will pass any type of Ethical hacking certifications and tests
The membership program also has a 30 day money back guarantee, so you have nothing to loose!, If you are unhappy with them, then they will return your every penny
So what are you waiting for, Don't wait until you loose your chance!Get it now!
 Labels:
Hacking basics
Labels:
Hacking basics
 0
comments
0
comments